Compliance & Risk Assessment
In this dynamic environment, CyberMindr’s Continuous Threat Exposure Management providing the essential tools to proactively manage and mitigate these challenges.
By offering comprehensive insights, and automated risk assessment, CyberMindr empowers CISOs to stay one step ahead of the ever-present threats to their organization’s cybersecurity.


Why Choose Us?
Data Breaches &
Unauthorized Access
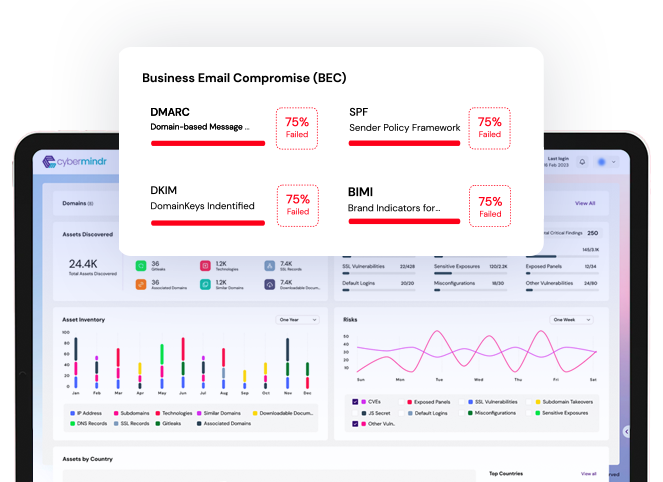
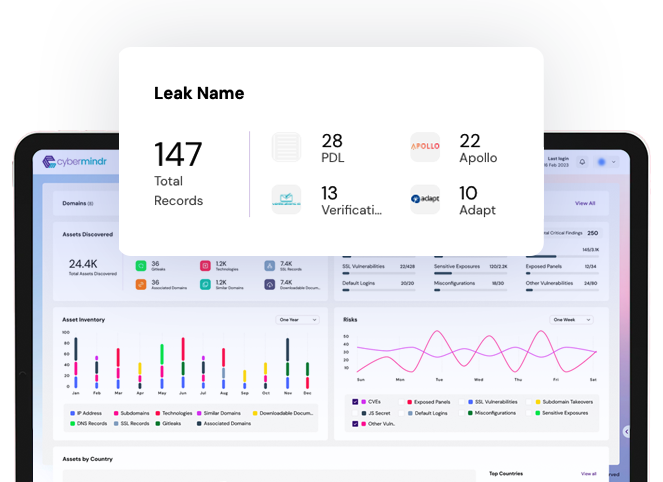
Third-party breaches can lead to unauthorized access of your sensitive data. Continuous threat exposure management can monitor the deep dark and surface web to identify potential attack surface.
Lack of
Visibility
Companies often lack visibility into third-party security practices. Continuous threat exposure management can provide insights into the security practices and vulnerabilities of technology partners for you to take necessary actions.
Security Patching and
Updating
Keeping third-party software and systems up to date can be difficult. Continuous threat exposure management can identify those vulnerabilities so that you can take necessary actions.
“Exposure is more than just the security posture.” – Gartner
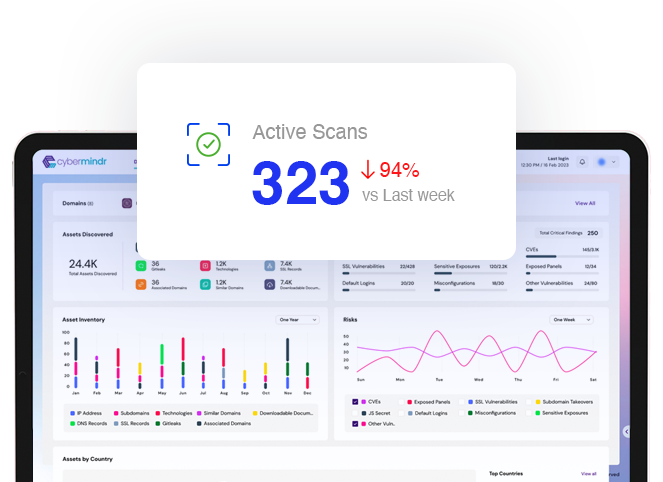
Platform
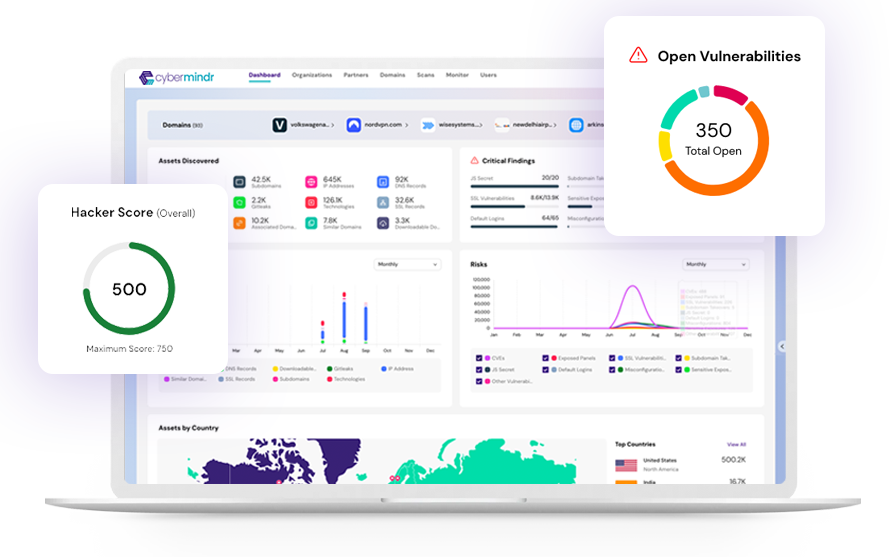
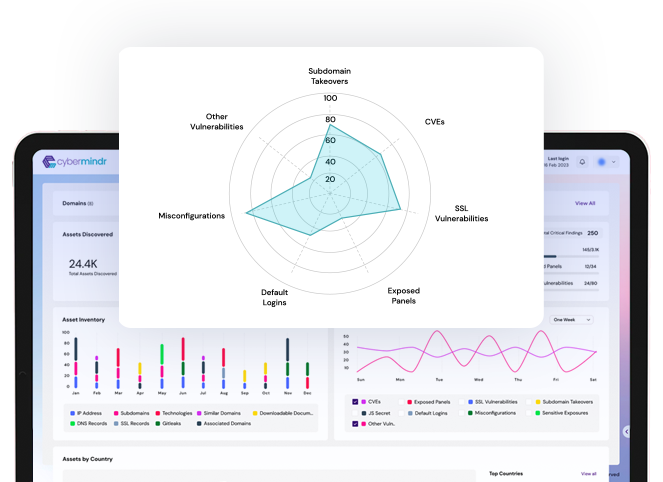
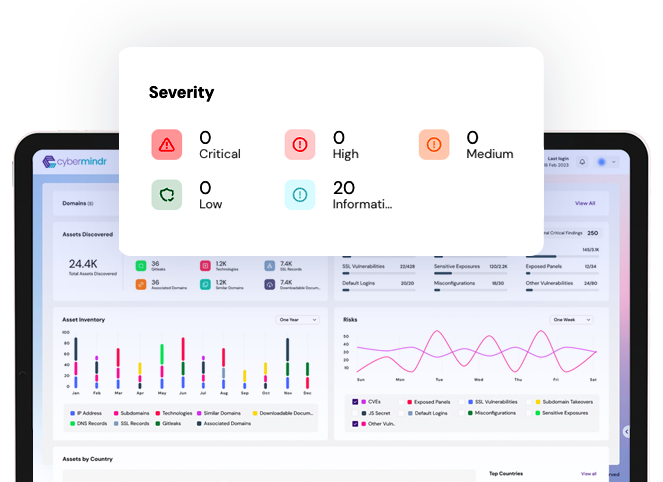
Continuously scan your internet facing assets for known and emerging vulnerabilities
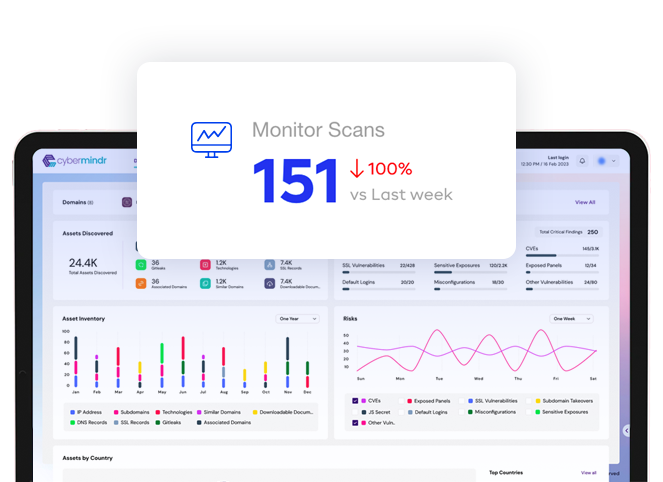
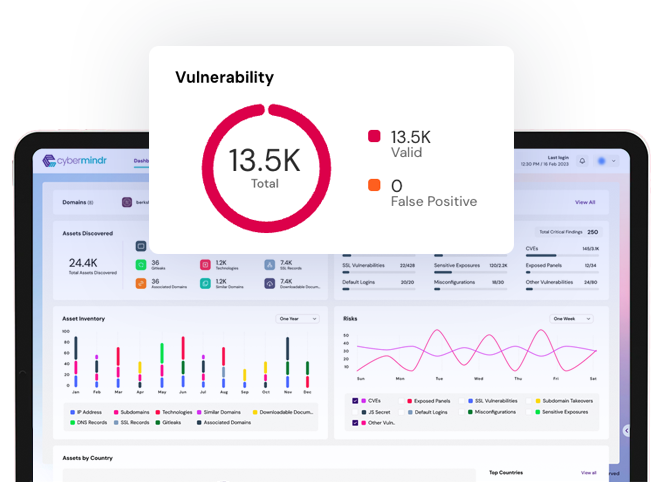
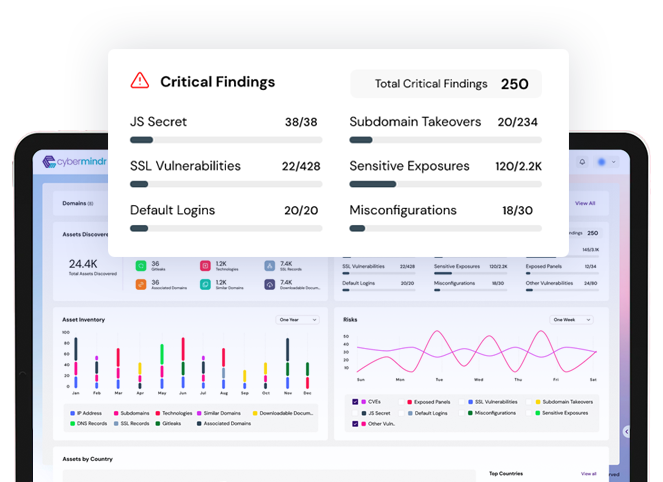
Advanced testing methods looks for vulnerabilities beyond CVEs
Related Use Cases

Gain insights into the cybersecurity posture of your portfolio companies
Read more

Gain insights into the cybersecurity posture of your portfolio companies
Read more

Meet regulatory requirements, streamline audits and avoid costly fines.
Read more

Conduct in-depth evaluations of potential acquisitions or partnerships.
Read more