CYBERMINDR USE CASE
Streamlining
Compliance & Risk
Management
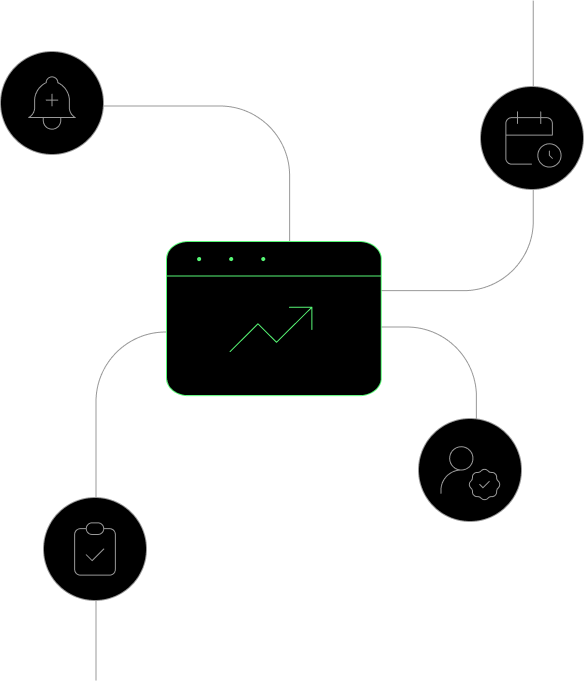
CyberMindr simplifies compliance with ISO 27001, SOC 2, and
NIST frameworks through CTEM and APD, enhancing security
and risk management