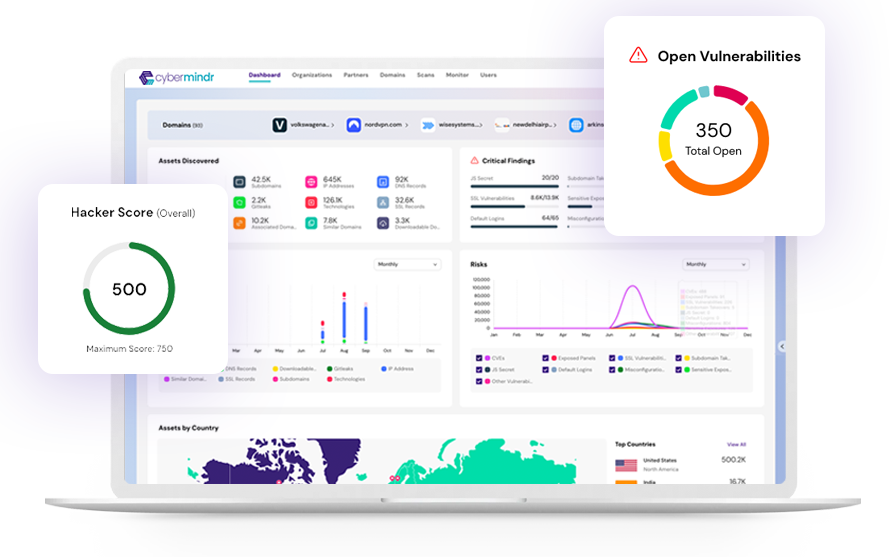
Compliance & Risk Assessment
Companies must navigate a minefield of challenges to ensure the security of their systems and the protection of sensitive data.
Continuous Threat Exposure Management, as a strategic & proactive approach helps organizations to streamline compliance efforts and enhance risk assessment procedures. It helps CISOs safeguard sensitive data and take timely steps to ensure adherence to intricate regulatory mandates.


Why Choose Us?
The complexity of modern IT environments, with a mix of on-premises, cloud, and hybrid systems, makes it challenging for a CISO to maintain compliance. CyberMindr helps you to gain visibility into a large part of your IT ecosystem, ensuring all assets are accounted for and assessed for compliance.
Safeguarding customer data and ensuring data privacy compliance is a growing challenge for companies. Continuous threat exposure management tools help organizations identify and address vulnerabilities that could provide a path to affect the privacy of customer data.
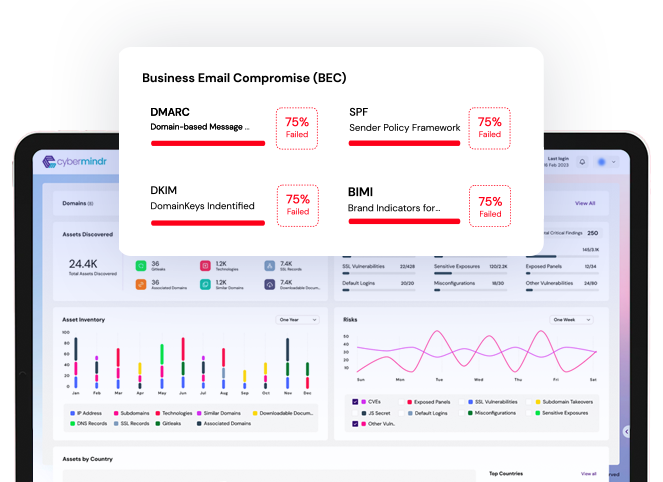
Companies operating in different geographies or verticals often have very demanding cybersecurity regulations, and compliance requirements. CyberMindr helps you to stay compliant with relevant regulations by providing continuous visibility into your security posture.
Most companies rely on a complex list of dependencies, making them susceptible to cyberattacks through third-party vendors or partner products. Continuous threat exposure management can help you to identify potential vulnerabilities before they are exploited.
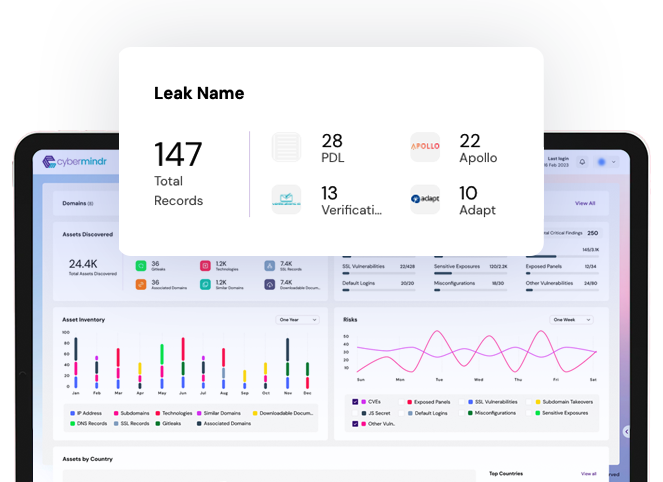
The CyberMindr discovery engine searches the dark web for leaked credentials that not only come from 3rd party data breaches but directly from malware infected devices.The platform helps you identify these compromises before they are leveraged by an attacker to gain access.
As businesses grow, managing compliance and risk assessment at scale becomes increasingly difficult. CyberMindr Platform for Continuous threat exposure management offers complete automation to handle the increased workload, making it easier to maintain compliance – even with limited resources.
“Exposure is more than just the security posture.” – Gartner
Platform
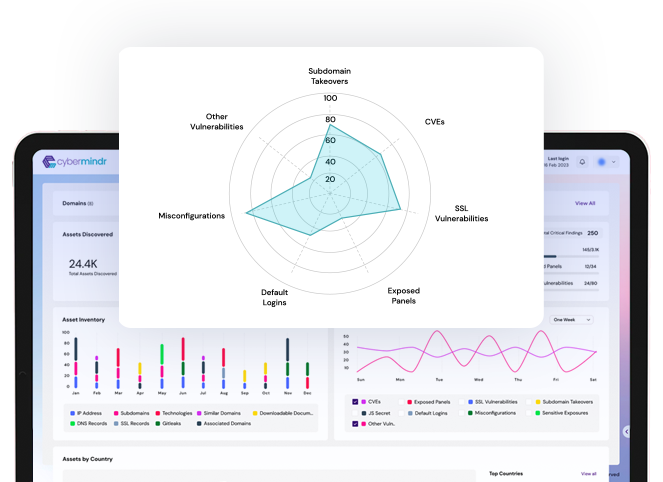
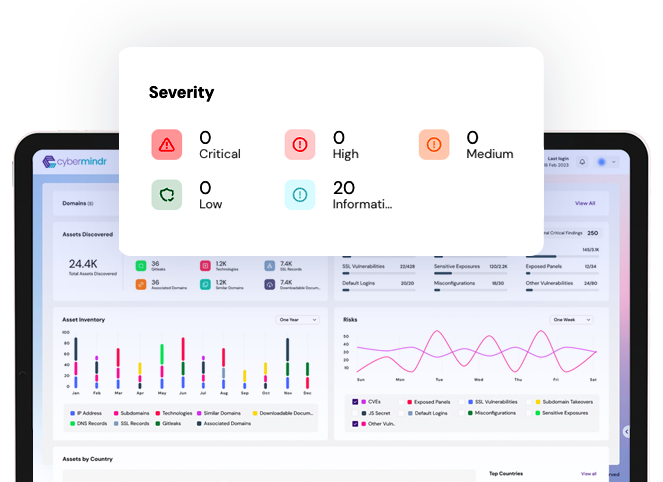
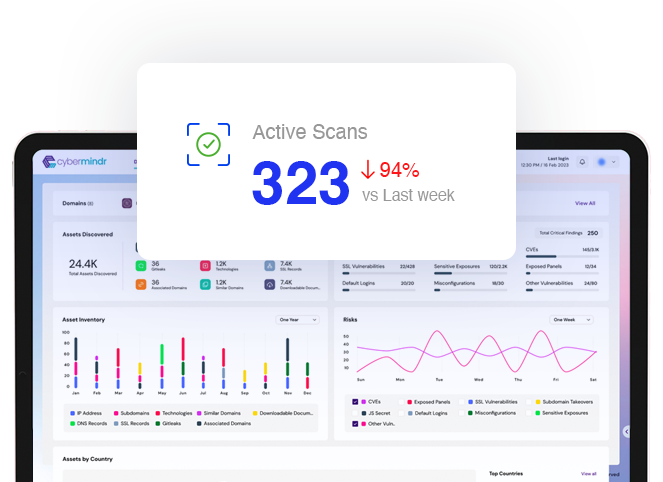
Continuously scan your internet facing assets for known and emerging vulnerabilities
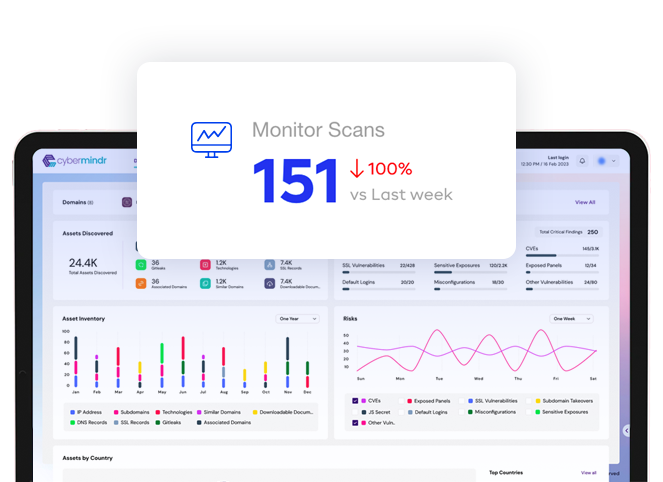
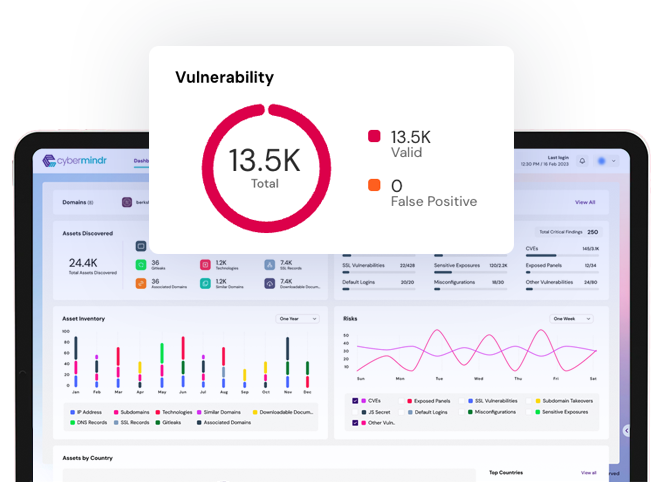
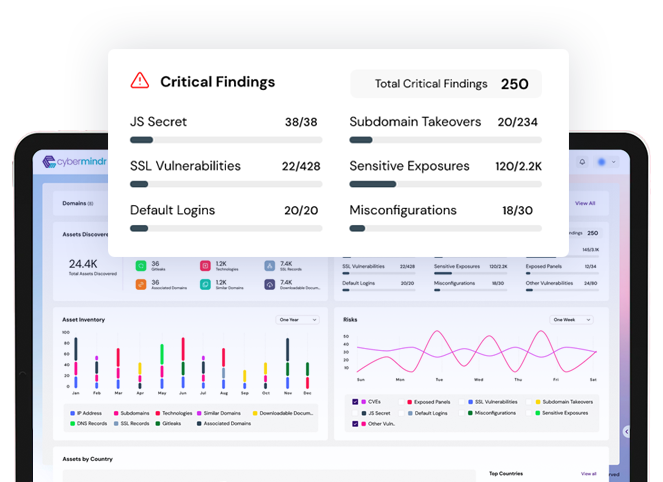
Advanced testing methods looks for vulnerabilities beyond CVEs
Related Use Cases
Pinpoint weaknesses in your security posture, prioritize remediation efforts, and fortify your defenses.
Read more

Gain insights into the cybersecurity posture of your portfolio companies
Read more

Safeguard your assets by minimizing potential risks from third party technologies that your organization uses.
Read more

Conduct in-depth evaluations of potential acquisitions or partnerships.
Read more