Discover Attack Paths
and their importance
Cyberattacks can occur when security procedures, coding techniques, or
IT infrastructure are not properly configured or when vulnerabilities are not
properly checked. These gaps can cause serious problems if we don't do
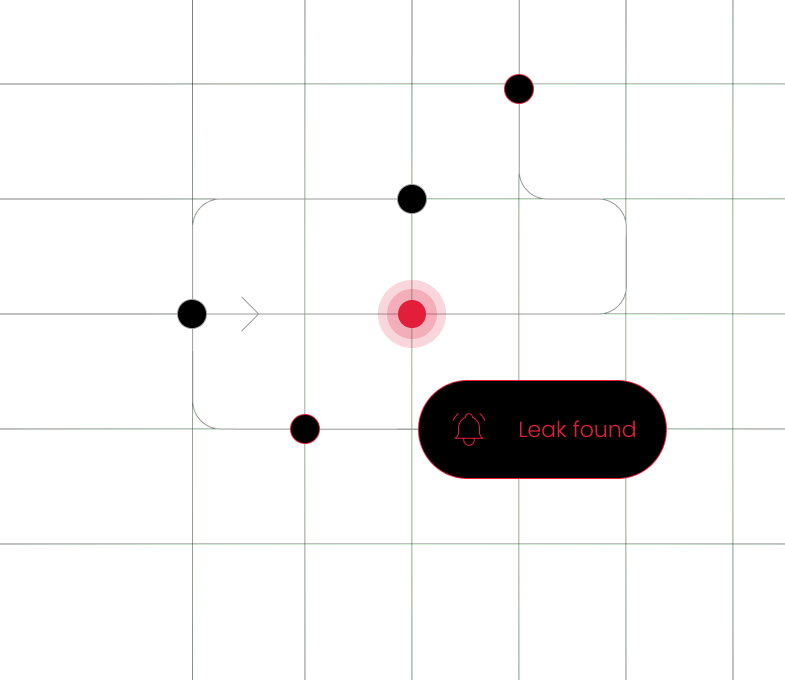
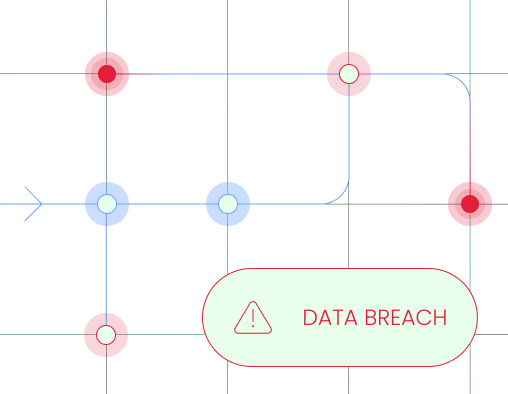
anything about them: A data breach occurs when private information is
leaked, which can damage the confidence of customers.
Downtime in Operations: Disruptions that impede the smooth running of
your company. Giving intruders authority over vital systems is an example
of unauthorized access. Possible fines for data protection failures due to
non-compliance.
The Threat of ransomware: A shackle for your vital files. Data exfiltration
refers to the disappearance of sensitive or important data.