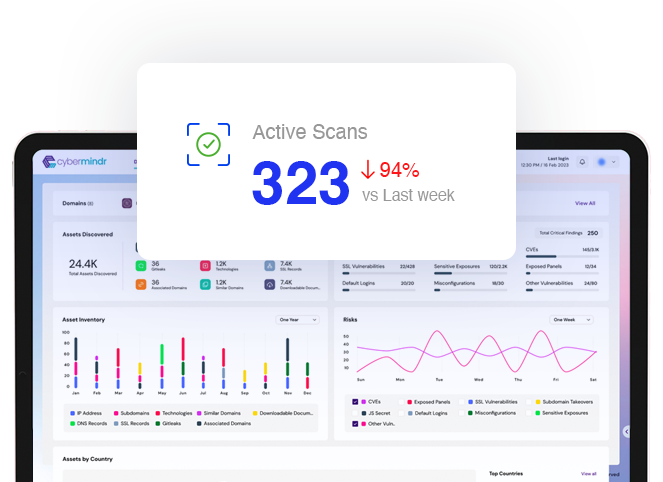
Overview
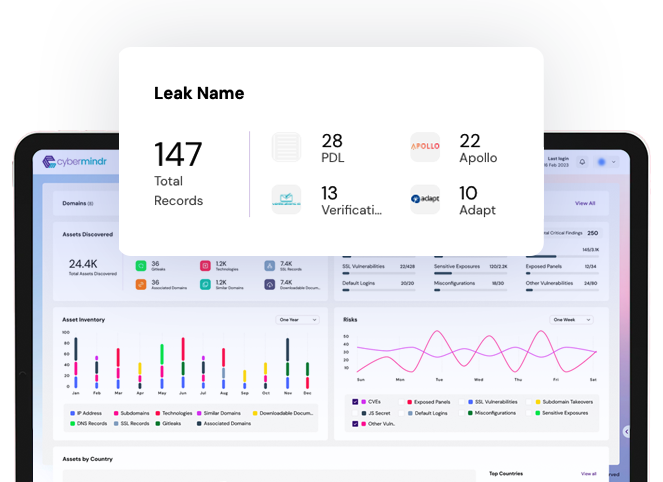
With continuous and automated monitoring, you can gain complete visibility into all aspects of a network, identifying hidden assets, misconfigured servers, open ports, and vulnerable endpoints. Automated threat detection tools help organizations move beyond manual or periodic scans, continuously checking for vulnerabilities, exposed credentials, and indicators of compromise in real time.
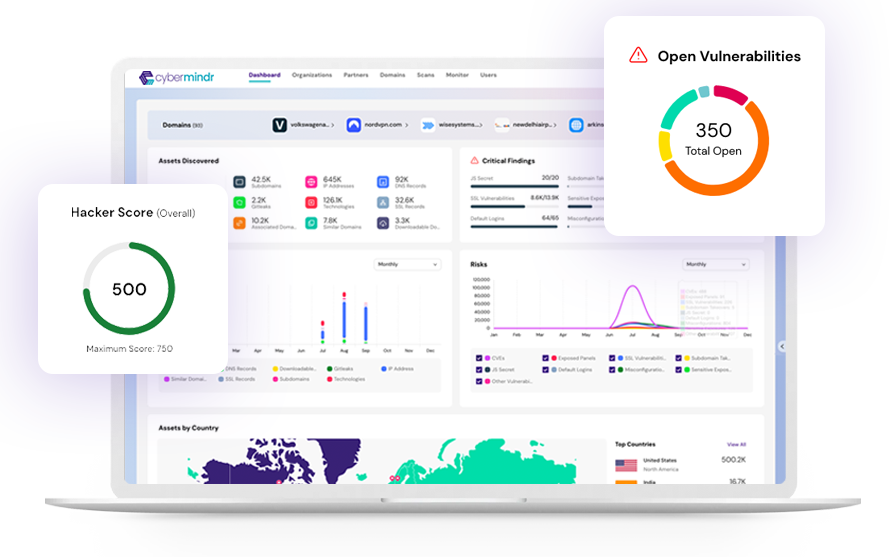

Why Choose Us?
Stay a step ahead of threats with real-time updates on vulnerabilities, malware infections, and external exposures that could put your business at risk.

Get automated alerts and actionable insights so your team can focus on critical issues without wasting resources on false alarms.
Ensure full visibility and control, whether you are monitoring 10 or 10,000 assets.
Get precise, data-driven insights to make informed security decisions and mitigate risks effectively based on real-time intelligence.
Stay on track with compliances and ensure meeting regulatory requirements by providing detailed logs, reports and security metrics.
Achieve comprehensive visibility into every aspect of your network with continuous scans to identify and monitor all assets.
Platform
Continuously scan your internet facing assets for known and emerging vulnerabilities
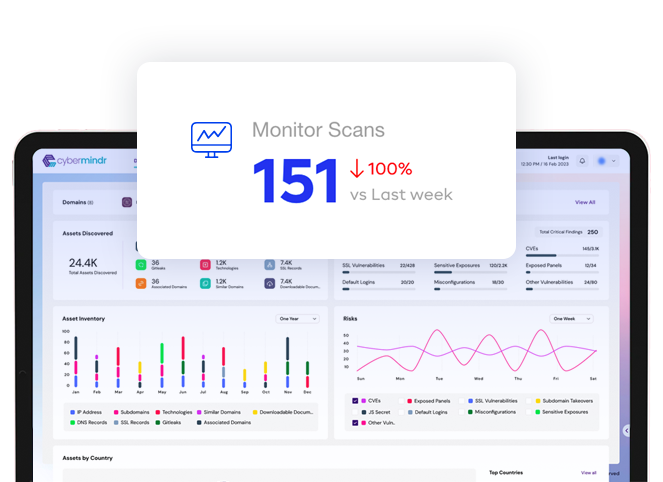
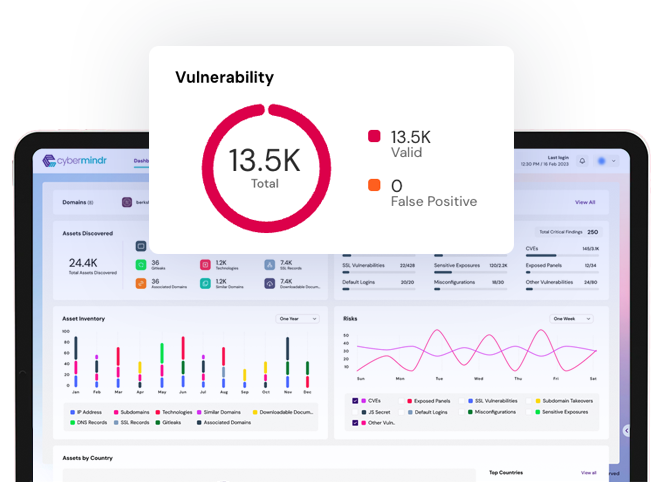
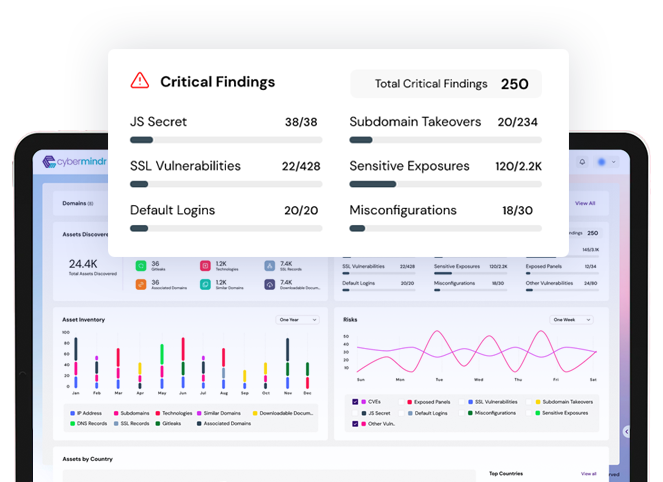
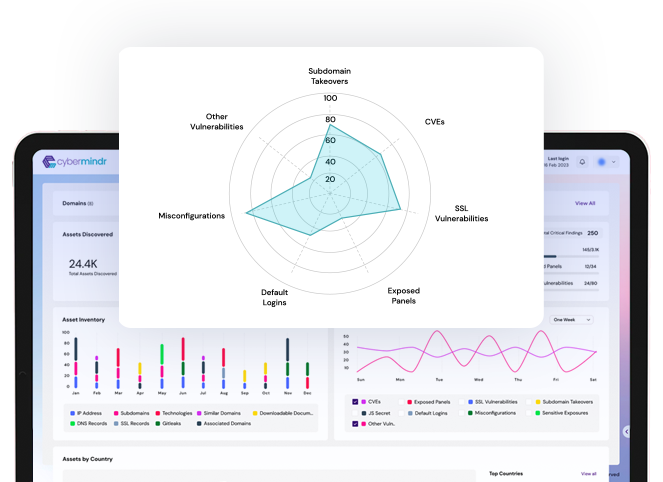
Advanced testing methods looks for vulnerabilities beyond CVEs
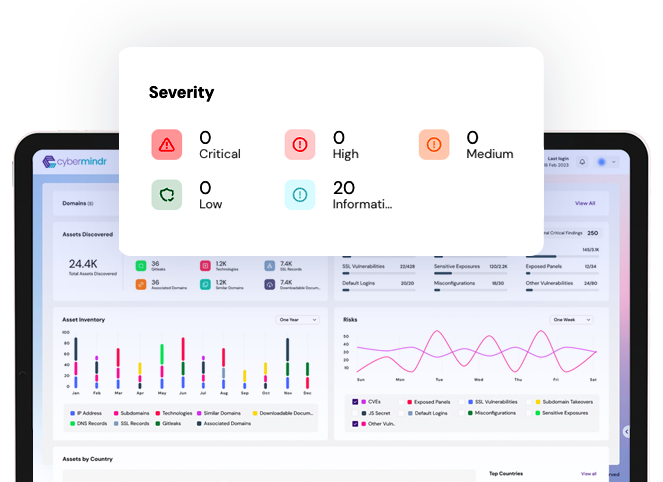
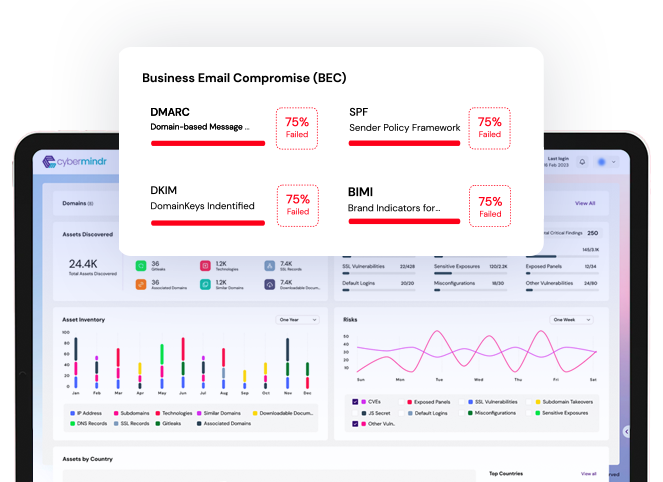

Related Use Cases
Pinpoint weaknesses in your security posture, prioritize remediation efforts, and fortify your defenses.
Read more

Gain insights into the cybersecurity posture of your portfolio companies
Read more

Safeguard your assets by minimizing potential risks from third party technologies that your organization uses.
Read more

Conduct in-depth evaluations of potential acquisitions or partnerships.
Read more