Proactively Protect
What Matters




The Power of
Preemptive Security

Next Gen
Asset Discovery
Go beyond OSINT based
solutions to actively discover
all your assets

Multi-stage
Attack Engine
Test for advanced complex
attacks based on emerging
threat intelligence

Near Zero
False Positives
Active Validation eliminates
noise, keeping your focus on
true threats
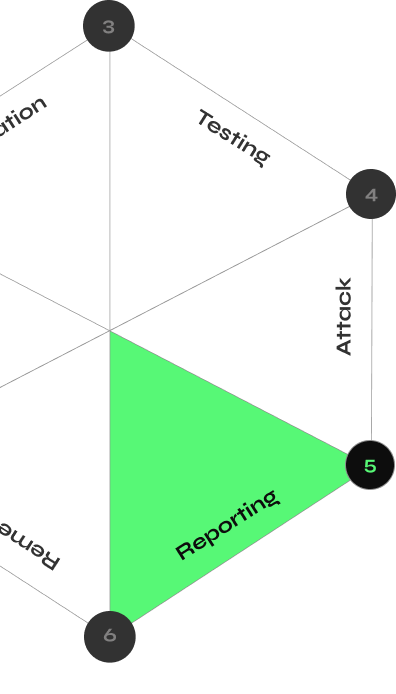
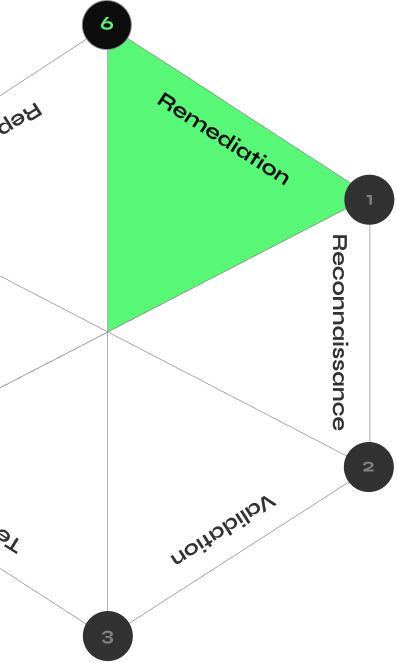
CYBERMINDR PLATFORM
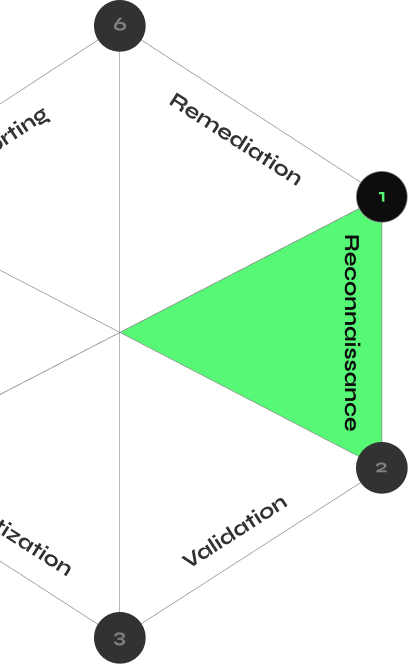
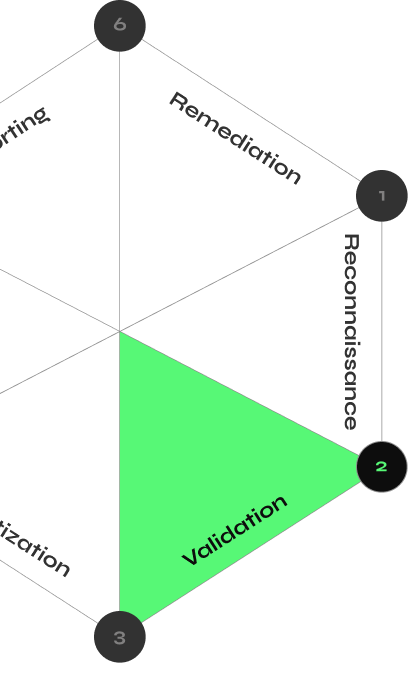
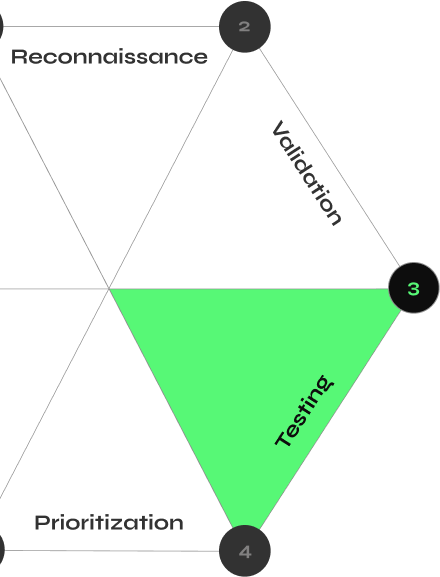
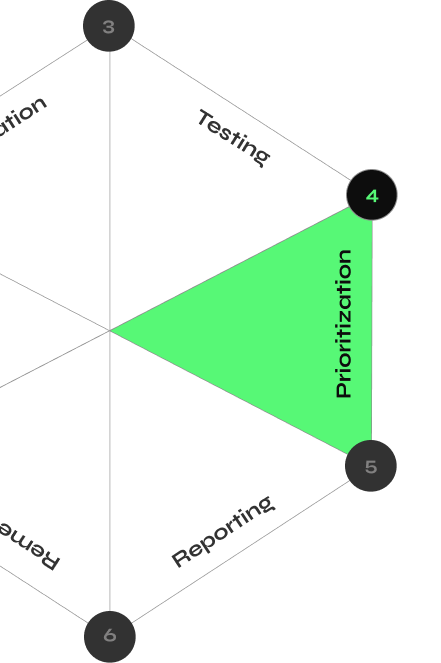
How CyberMindr Works
Discover validated attack paths with an automated multi-stage attack engine

100%
Automated

Near Zero
False-positives
Use Cases
Proactive Cyber Protection
for Business Continuity

Attack Path Discovery
Identify security weaknesses, prioritize remediation, and strengthen defenses.

Threat Exposure Validation
Scan the internet to uncover known, unknown and unmonitored digital assets

Portfolio Risk Assessment
Gain insights into the cybersecurity posture of your portfolio companies

Compliance & Risk Assessment
Meet regulatory requirements, streamline audits and avoid costly fines

Cyber Security Due Diligence
Conduct in depth evaluations of potential acquisitions or partnerships

Cyber Insurance Security
Minimize risk for third-paty technologies to safeguard your assets
The Value Of
One Platform
CyberMindr focuses on validated vulnerabilities and
confirmed attack paths,
performing 16,000+ live checks on discovered assets. Continuously updated
with
intelligence from 300+ hacker forums, CyberMindr helps you prioritize
remediation
with precision, targeting real threats before they are exploited.
CyberMindr focuses on validated vulnerabilities and confirmed attack paths, performing 16,000+ live checks on discovered assets. Continuously updated with intelligence from 300+ hacker forums, CyberMindr helps you prioritize remediation with precision, targeting real threats before they are exploited.
Book a Demo1 M+
Vulnerabilities Found
10 M+
Assets Monitoring
300+
Hackers Forums Monitored
100K+
Detected Attack Paths
Visibility. Verification. Validation
Proactive Cyber Protection
For Business
Continuity
Experience visibility through the hacker’s lens with an AI-powered, integration-free platform. Run continuous scans of your digital landscape, uncovering real attack paths and vulnerabilities, delivering proactive, validated security. Automate threat detection and prioritization for quick remediation, ensuring continuous protection.
Book a DemoClient Testimonial
We don't waste our time on false positives anymore
CyberMindr has helped us focus our remediation efforts where they actually matter. Unlike other tools, CyberMindr delivers validated vulnerabilities and confirmed attack paths, giving our security team clear, actionable insights.
— CISO, Leading Mailing & Shipping Solutions Provider

Resources
Frequently Asked Questions
Key features of CyberMindr include:
Third-Party Exposures – Detect risks from vendors and external services.
Phishing Protection – Assess DMARC, SPF, DKIM, and BIMI configurations to enhance anti-phishing posture.
Dark Web Monitoring – Track exposed credentials and data leaks.
Git Leaks – Find sensitive information unintentionally exposed in Git repositories.
Developer Exposures – Detect publicly accessible code, exposed API keys, and hidden files posing security risks.
Botnet Infections – Detect if your assets are compromised by botnets.
Compliance Tracking – Monitor and support regulatory compliance.
CyberMindr only needs your domain name to run scans, it works entirely outside your network. It does not request access or permissions to view your data.
Reports may include sensitive information already exposed through OSINT, or found on the deep and dark web. CyberMindr follows strict policies to keep reports confidential and uses encryption to protect all sensitive information.
CyberMindr's pricing depends on the size of your domain and the number of subdomains. You can choose between a one-time scan or recurring scans (daily, weekly, or monthly).
There is no free basic plan, but if you have received a free scan, you can still opt for a one-time scan.
CyberMindr follows the MITRE ATT&CK framework and helps you take a proactive approach to security. It scans the internet, including the deep and dark web to uncover real threats linked to your domain, such as exposed credentials, phishing sites, and developer leaks.
The platform provides verified findings and actionable steps so you can fix issues before they turn into attacks.
Evaluating the security maturity of a potential partner helps identify long-term risks that go beyond surface-level exposures, such as weak security practices, unmanaged assets, or lack of control visibility.
CyberMindr supports this process by uncovering signs of poor cyber hygiene, like outdated infrastructure, credential leaks, and misconfigurations across external assets. These insights help organizations assess risk levels, make informed decisions, negotiate terms, and plan post-merger integration priorities.