Proactively Protect
What Matters




The Power of
Preemptive Security

Next Gen
Asset Discovery
Go beyond OSINT based
solutions to actively discover
all your assets

Multi-stage
Attack Engine
Test for advanced complex
attacks based on emerging
threat intelligence

Near Zero
False Positives
Active Validation eliminates
noise, keeping your focus on
true threats
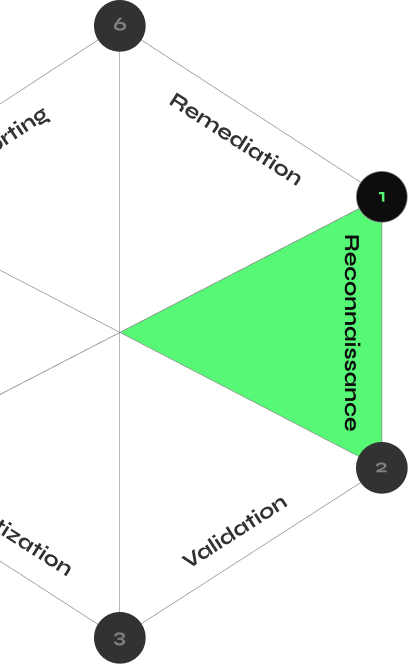
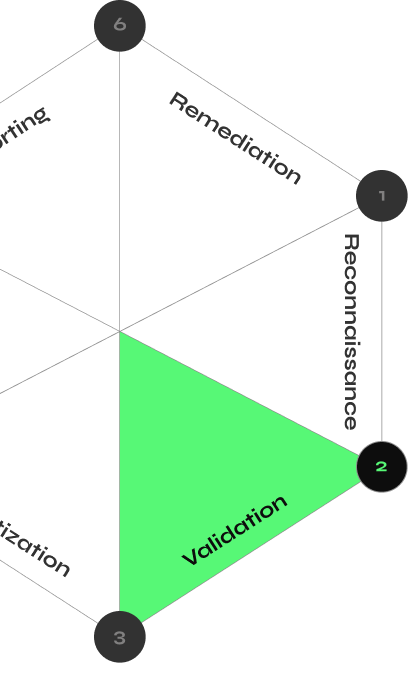
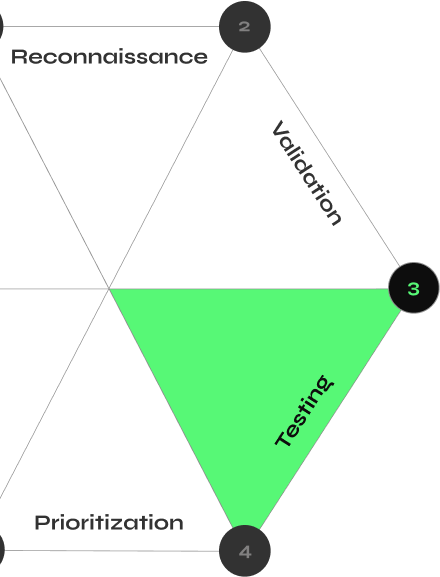
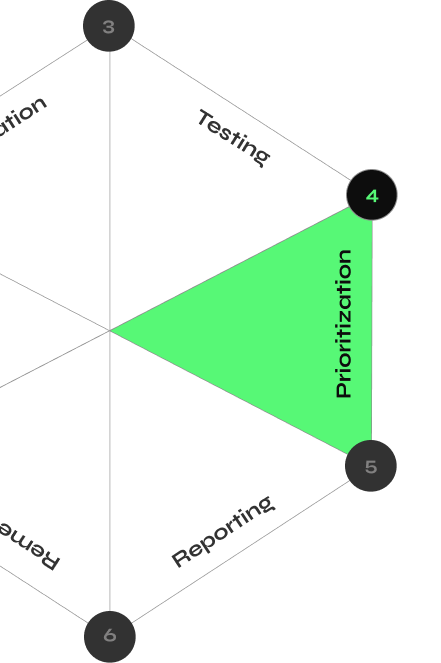
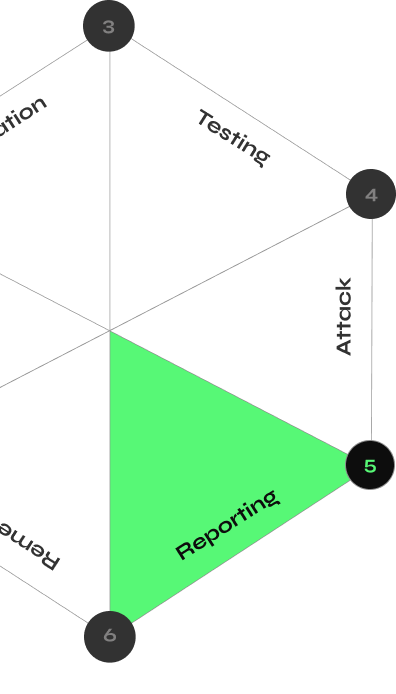
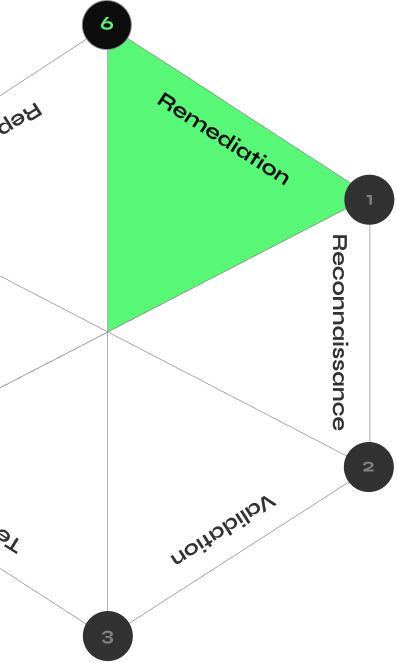
CYBERMINDR PLATFORM
How CyberMindr Works
Discover validated attack paths with an automated multi-stage attack engine

100%
Automated

Near Zero
False-positives
Use Cases
Proactive Cyber Protection
for Business Continuity

Attack Path Discovery
Identify security weaknesses, prioritize remediation, and strengthen defenses.

Threat Exposure Validation
Scan the internet to uncover known, unknown and unmonitored digital assets

Portfolio Risk Assessment
Gain insights into the cybersecurity posture of your portfolio companies

Compliance & Risk Assessment
Meet regulatory requirements, streamline audits and avoid costly fines

Cyber Security Due Diligence
Conduct in depth evaluations of potential acquisitions or partnerships

Cyber Insurance Security
Minimize risk for third-paty technologies to safeguard your assets
The Value Of
One Platform
CyberMindr focuses on validated vulnerabilities and
confirmed attack paths,
performing 16,000+ live checks on discovered assets. Continuously updated
with
intelligence from 300+ hacker forums, CyberMindr helps you prioritize
remediation
with precision, targeting real threats before they are exploited.
CyberMindr focuses on validated vulnerabilities and confirmed attack paths, performing 16,000+ live checks on discovered assets. Continuously updated with intelligence from 300+ hacker forums, CyberMindr helps you prioritize remediation with precision, targeting real threats before they are exploited.
Book a Demo1 M+
Vulnerabilities Found
10 M+
Assets Monitoring
300+
Hackers Forums Monitored
100K+
Detected Attack Paths
Visibility. Verification. Validation
Proactive Cyber Protection
For Business
Continuity
Experience visibility through the hacker’s lens with an AI-powered, integration-free platform. Run continuous scans of your digital landscape, uncovering real attack paths and vulnerabilities, delivering proactive, validated security. Automate threat detection and prioritization for quick remediation, ensuring continuous protection.
Book a DemoClient Testimonial
We don't waste our time on false positives anymore
CyberMindr has helped us focus our remediation efforts where they actually matter. Unlike other tools, CyberMindr delivers validated vulnerabilities and confirmed attack paths, giving our security team clear, actionable insights.
— CISO, Leading Mailing & Shipping Solutions Provider